Modifying Security Settings for Ripple Users
Custom Security Settings
Ripple provides customizable security settings to help teams control access levels based on institutional requirements. Site Admins should regularly review these settings and consult their institution’s IT security guidelines to ensure compliance.
How to Edit Security Settings
- Go to Site Admin – Navigate to the Site Admin tab (green).
- Access Security Settings – Click on the Security section (red).
- Adjust Security Preferences – Modify the settings as needed based on team preferences or institutional policies.
- Save Changes – Ensure all changes are saved to apply updated security settings.
Regularly reviewing and updating these settings helps maintain compliance and protect sensitive data.
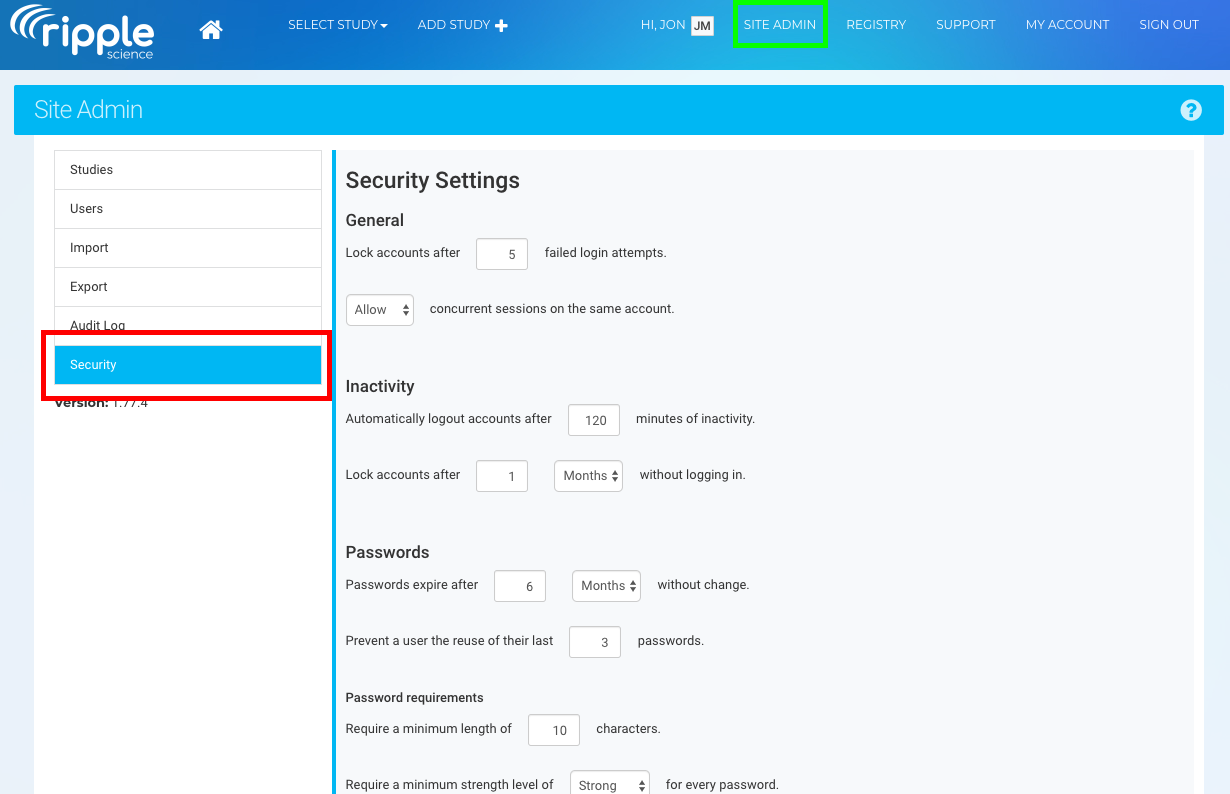
General Security Settings
Ripple allows administrators to configure security settings to enhance account protection and comply with institutional policies. Below are key security settings that can be adjusted:
1. Login Attempts
- Set the number of unsuccessful login attempts allowed before an account is locked.
- Example: If set to 5, a user entering the wrong password 5 consecutive times will have their account locked.
- Unlocking Accounts: A Site Administrator must unlock the account via the Team menu in the Site Admin dashboard.
2. Simultaneous Sessions
- By default, Ripple prevents simultaneous active sessions by the same user.
- If a user logs in from a different browser or device, the original session will be terminated.
- Customizing the Setting: Administrators can allow simultaneous sessions, but this may conflict with institutional security policies.
- Important: Most institutions do not allow sharing of user credentials for systems managing personal data. Consult IT before changing this setting.
Administrators should review these settings regularly to ensure they align with institutional security policies.
Inactivity Security Settings
Ripple allows Site Administrators to configure inactivity settings to enhance security and prevent unauthorized access.
1. Automatic Logoff
- Defines the inactive session time limit before a user is automatically logged out.
- Importance: Prevents unauthorized access if a user forgets to log out.
- Recommended Setting: Maximum 10 minutes of inactivity before logoff.
2. Automatic Lock of Unused Accounts
- Accounts are automatically locked if they remain unused for a specific period.
- Best Practice: Lock accounts after 3 months of inactivity, especially for systems managing health information.
- Unlocking Accounts: A Site Administrator must manually unlock inactive accounts when needed.
Regularly reviewing these settings ensures compliance with security best practices and institutional policies.
Password Security Settings
Ripple allows Site Administrators to enforce password policies to enhance account security. Below are the configurable password settings:
1. Password Expiration
- Administrators can set an expiration period for user passwords.
- Action: Check your institution’s password expiration guidelines to ensure compliance.
2. Password Reuse Restriction
- Prevents users from reusing past passwords upon reset.
- Default Setting: Ripple blocks reuse of the last 4 passwords by default.
- Customizable: Administrators can adjust the number of previously used passwords that are restricted.
3. Password Minimum Length
- Defines the minimum number of characters required for passwords.
- Action: Set a length that balances security and usability.
4. Password Strength Enforcement
- Ripple uses the zxcvbn algorithm to assess password strength.
- Recommendation: Set to at least "moderate" to ensure strong passwords.
5. Password Character Requirements
- Administrators can enforce specific character requirements, such as:
- Numbers (0-9)
- Symbols (@, #, $, etc.)
- Action: Adjust settings based on security policies of your institution.
Regularly reviewing these settings ensures strong password security and compliance with institutional policies.
